Your enterprise doesn’t need to be multinational to suffer significant losses – a single cyber incident can halt operations, damage consumer trust, and cost thousands of dollars.
Recent research indicates that the average data breach price has reached $4.4 million (Source: IBM) globally, with small firms experiencing closure rates of 60% (Source: Verizon) within six months of a major cyberattack. These cybersecurity statistics underline why partnering with a proven cybersecurity services provider is no longer optional.
A robust cybersecurity risk management plan can turn this hazard into a solvable checklist.
This guide is built for you if you’re:
Here’s what you will get from this cybersecurity risk management program:
In this article, we’ll show you the way to build cyber resilience through clever cyber security risk management that fits your budget and resources.
What is a Cybersecurity Risk Management Plan?
A cybersecurity risk management plan is a comprehensive, ongoing method that enables companies to identify, verify, and mitigate potential threats to their digital assets.
It’s a strategic approach to proactively mitigate dangers related to cyberattacks, ensuring business continuity and protecting sensitive information.
Core Components of Cybersecurity Risk Management Plan
Every solid security management plan includes these building blocks:
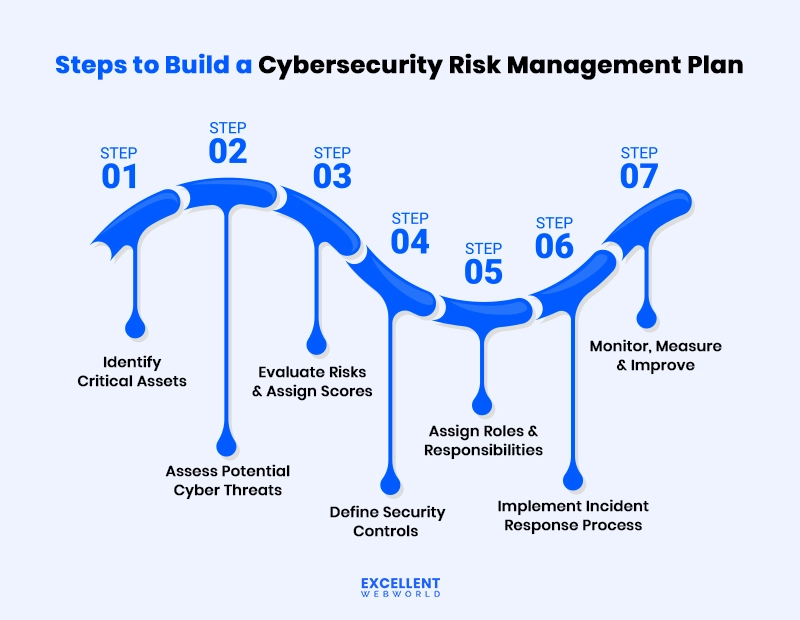
How to Create a Cybersecurity Risk Management Plan in 7 Simple Steps
Now that you understand why cybersecurity risk management is critical for your business success, here’s how to build your comprehensive risk management plan step by step:
Let’s get into the nitty-gritty of each step in the upcoming sections.
Step 1: Identify Critical Assets & Data
You can’t protect what you don’t know exists. Before building your cybersecurity management plan, you need a complete picture of everything valuable in your business.
So, what Counts as an Asset?
Your assets fall into seven main categories:
Many companies overlook IoT and hardware-level threats — see our insights on embedded systems security for better protection.
How to Build Your Asset Inventory? Building a comprehensive asset inventory is the critical first step in developing an effective enterprise cybersecurity strategy and risk management framework.
Here is a 3-week plan of how to build your asset inventory:
📥 Download the Asset Inventory Template
Use this template to build a consolidated asset repository and keep track of all your critical assets efficiently.
Your cyber risk management program depends on this accuracy.
Your enterprise cyber risk management strategy starts with knowing exactly what you’re protecting. This inventory becomes the foundation for threat modeling and your incident response plan.
Remember: Your cyber risk management policy is only as firm as the asset inventory supporting it.
Step 2: Assess Potential Cyber Threats & Vulnerabilities
You need to know what you’re protecting against before building defenses. This step creates your threat baseline, informed by an analysis of recent cyber attacks and proven methods that work for businesses of your size.
To understand your threat landscape, Start with STRIDE threat modeling – a simple framework that breaks down cyber risks into six categories:
Now we’ll understand how to find your potential vulnerabilities. A solid cyber risk strategy requires regular vulnerability checks through multiple methods:
| Method | Actions | Frequency | Tools / Examples |
|---|---|---|---|
| Automated Security Scans | Monthly | Nessus, OpenVAS | |
| Annual Penetration Testing | Annually | Professional penetration testing services | |
| Configuration Reviews | Quarterly | CIS Benchmarks | |
| Human Risk Assessment | Every 3 months | Phishing Simulation Platforms | |
| Third-Party Risk Checks | As Needed / Contract renewal | SOC reports, Contract audits |
This comprehensive security assessment framework provides a structured approach to identifying vulnerabilities through both technical testing and human factor evaluation.
Documenting Risk Scenarios: Creating an effective cyber risk mitigation plan starts with documenting realistic scenarios your business might face.
📥 Download the Threat Scenarios Template
Use this template to capture, analyze, and prepare for potential cyber risk scenarios in your organization.
This approach creates a practical security risk mitigation plan that connects directly to your business assets. When you map threats to specific systems, your risk mitigation strategies become much more focused.
Building this plan requires recognizing the scale of the threat. Our COO, Mahil Jasani, has published a fascinating and sobering analysis on this very topic. Don’t miss it: How Many Cyber Attacks Happen Per Day? by Mahil Jasani, COO.
Step 3: Evaluate Risks & Assign Scores
You’ve identified your risks. Now you need to figure out which ones deserve your immediate attention and limited budget.
How Do You Score Cybersecurity Risks? Effective cybersecurity risk management starts with proper scoring. By quantifying threats, organizations can prioritize resources and address the most critical vulnerabilities first.
Use this simple formula: Risk Score = Likelihood × Impact
Rate both on a 1-5 scale, where 1 is very low and 5 is very high. This gives you scores from 1-25.
Example 1: Data Breach Risk
Example 2: Office Printer Failure
📥 Download the Risk Register Template
Use this template to track, assess, and manage all identified risks in one central place.
How Do You Prioritize Your Risk List? Sort risks using this three-step approach to build effective cyber risk mitigation planning:
What About Residual Risk?
After you implement controls, re-score your risks. For example, if email phishing had a score of 20 (Likelihood 4 × Impact 5), adding email filtering might reduce the likelihood to 3, giving you a new score of 15. This shows your progress and validates your cyber risk mitigation strategies.
Your cybersecurity risk management policy must include monthly risk register updates. This keeps your cyber risk management strategy aligned with evolving threats.
Step 4: Define Security Controls & Preventive Measures
Time to build your defense system. You need to match each risk with specific protections that work for your business.
There are three types of security controls you need to protect your business effectively. Modern businesses need three essential security layers working together: administrative policies, technical safeguards, and physical barriers for complete protection. Let’s analyze them in detail.
| Administrative Controls: | |
| Technical Controls: | |
| Physical Controls: |
To stay organized, Create Your Risk-to-Control Mapping Table. Your cybersecurity risk management plan needs a simple tracking system:
Risk identified → Recommended control → Owner → Cost → Deadline
For Example:
Risk: Employee email compromise → Multi-factor authentication → IT Manager → $50/month → March 15th
This organized approach helps with effective cybersecurity program development.
Once you have your mapping table ready, you need to know what to tackle first. This is where the Priority Implementation List comes in.
Here’s your priority order:
| Phase One – Highest Impact: | |
| Phase Two – Network Protection: |
When building cybersecurity plans, focus on cybersecurity risk mitigation that fits your budget. Document each control with clear acceptance criteria.
Effective cyber security planning involves implementing risk management strategies in a step-by-step approach, rather than overwhelming your team with everything at once.
If you are not comfortable managing all these tasks alone, consider connecting with a cybersecurity services provider. They can assess your security posture and help you develop a plan that suits your budget and needs.
Step 5: Assign Roles & Responsibilities (RACI)
Who does what when cyber threats hit your business? Without clear roles, your team will scramble while attackers move fast.
Start with these key people in your business:
Even small teams can assign multiple roles to one person. The key is knowing who owns what. Use a RACI matrix to map out who is responsible, accountable, consulted, and informed for each security task.
For example, while creating an asset inventory, RACI would look like:
Now use your RACI roles to create escalation paths. Each person in your matrix becomes part of your response chain. Create a simple phone tree for different threat levels:
| Low Risk: [Spam emails, minor software glitches] | |
| Medium Risk: [Suspicious login attempts, potential data exposure] | |
| High Risk: [Confirmed ransomware, active data breach, system shutdown] |
Your SOC (Security Operations Center) or monitoring service should have this escalation tree printed and easily accessible.
Pick one person to own your entire cybersecurity risk management plan. This person reviews it every six months and updates contact lists.
Step 6: Implement Incident Response Procedures
When cyber attacks hit your business, you need a plan that works fast. Your cyber security risk management process depends on quick, smart responses.
Master incident response with our proven framework. Below are the six critical phases every security team needs:
For organizations without an in-house team, partnering with one of the best incident response companies ensures rapid detection, containment, and recovery.
Now, let’s look at what key actions you need to take for a particular phase with a hypothetical example.
Monday 9:15 AM – Crisis Hits Your Business
Your accounting team panics: “We can’t open any files!”
Here’s how your six phases save the day:
| Phase | Key Actions | Ransomware Attack Example & Timeline |
|---|---|---|
| 1. Detect | Your digital early warning system – comprehensive monitoring that spots trouble before it spreads. | (9:15 AM) |
| 2. Triage | Smart decision-making under pressure – structured assessment that cuts through chaos to prioritize correctly. | (9:17 AM) |
| 3. Contain | Digital quarantine in action – immediate isolation that stops attackers cold in their tracks. | (9:20 AM) |
| 4. Eradicate | Complete threat elimination – thorough investigation and removal that leaves no malicious trace behind. | (9:30 AM) |
| 5. Recover | Safe restoration to normal operations – verified clean systems that get business running again. | (10:00 AM) |
| 6. Learn | Post-incident wisdom – transforming painful experience into stronger defenses that prevent future attacks completely. | (End of Day) |
Step 7: Monitor, Measure & Improve
This proven framework transforms security chaos into a structured response, protecting your business when attacks strike.
Your Daily Security Health Check
Set up simple monitoring tools that watch your business 24/7:
- SIEM system – collects all security logs in one place
- EDR tools – monitor your computers and devices
- NDR solutions – watch your internet traffic
- Threat intelligence feeds – alert you about new threats
- Vulnerability scanners – find weak spots in your systems
Create Your Monitoring Schedule
Your IT security risk management depends on consistent monitoring, not sporadic checks.
- Daily: Check security alerts and unusual activity
- Weekly: Run vulnerability scans on your systems
- Monthly: Review your security posture dashboard
- Quarterly: Test if your security controls still work
Measure What Matters
Track meaningful cyber security KPIs:
- How quickly can you detect threats
- Time to patch vulnerabilities
- Number of security incidents
- Employee security training completion
The Improvement Loop
Follow the Plan-Do-Check-Act cycle:
- Plan – Identify what needs improvement
- Do – Implement new security measures
- Check – Test if changes work
- Act – Make permanent updates
When you find gaps in your cyber risk protection, document what you learned. Update your procedures and train your team.
Security governance means continuous learning, not set-and-forget. Regular threat hunting exercises help you stay ahead of attackers.
Download Free Editable Cybersecurity Risk Management Plan Template
Drawing from our extensive cybersecurity expertise and proven risk management frameworks, we’ve developed this comprehensive, editable template collection to help organizations build effective security programs.
Download Your Complete Risk Management Toolkit
📋 Complete Template Package Includes:
Industry-Specific Cybersecurity Risk Management Plans
Effective cybersecurity risk management solutions require industry-specific approaches tailored to unique assets, threats, and regulatory requirements for optimal protection.
Here are the industry-specific risk management plans that may help you out:
1. Startup/SMBs
| Top Assets: | Customer data, IP, email systems, cloud accounts |
| Top Risks: | Phishing, ransomware, weak passwords, unpatched systems |
| Quick Wins: | MFA, employee training, automated backups, endpoint protection |
| Tools: | Microsoft Defender, Google Workspace Security, KnowBe4, Veeam |
| Compliance Notes: | GDPR/CCPA basics, cyber insurance |
2. Banking/Finance
| Top Assets: | Customer financial data, transaction systems, trading platforms, regulatory reports |
| Top Risks: | Advanced persistent threats, insider threats, DDoS attacks, fraud |
| Quick Wins: | Network segmentation, privileged access management, real-time monitoring, encryption |
| Tools: | Splunk, CrowdStrike, Varonis, IBM QRadar, Proofpoint |
| Compliance Notes: | SOX, PCI DSS, FFIEC guidelines, GLBA |
3. Healthcare
| Top Assets: | Patient records (PHI), medical devices, research data, imaging systems |
| Top Risks: | Ransomware, medical device vulnerabilities, insider threats, data breaches |
| Quick Wins: | Device inventory, access controls, data encryption, incident response plans |
| Tools: | Palo Alto Networks, Symantec, Tenable, FireEye, Epic security modules |
| Compliance Notes: | HIPAA, HITECH Act, FDA cybersecurity guidance |
4. SaaS/Cloud-Native
| Top Assets: | Customer data, APIs, microservices, container infrastructure, CI/CD pipelines |
| Top Risks: | API vulnerabilities, container escape, supply chain attacks, misconfigurations |
| Quick Wins: | Container security, API gateways, infrastructure as code, DevSecOps integration |
| Tools: | Aqua Security, Snyk, HashiCorp Vault, AWS GuardDuty, Kubernetes security tools |
| Compliance Notes: | SOC 2, ISO 27001, cloud provider compliance frameworks |
How AI & Automation Can Improve Risk Management?
AI and automation tools can help you spot threats faster and protect your business better than manual methods alone.
Here are the key benefits of using automation and generative AI in cybersecurity:
Learning how to handle zero-day vulnerabilities is also essential, as these are previously unknown software flaws that hackers can exploit.
Key Metrics & KPIs to Track Plan Success
You need clear numbers to determine if your cybersecurity plan is effective and protects your business. Here are the few cyber security KPIs that matter the most:
| Metric/KPIs | What does it mean? | Formula | Good Target |
|---|---|---|---|
| Mean Time to Detect (MTTD) | How fast can you spot a security problem | (Total time from attack start to discovery) ÷ (Number of incidents) | Under 24 hours |
| Mean Time to Respond (MTTR) | How quickly you fix security issues | (Total time from discovery to resolution) ÷ (Number of incidents) | Under 4 hours |
| Patch Compliance % | How many of your systems have the latest security updates | (Systems with latest patches ÷ Total systems) × 100 | 95% or higher |
| Phishing Click Rate | How many employees click on fake emails | (Employees who clicked ÷ Total emails sent) × 100 | Under 5% |
| High Residual Risks | Number of serious risks you haven’t fixed yet (score 15+) | Count of unresolved risks with a severity score ≥15 | Less than 5 |
| Backup Restore Success Rate | How often do your backups work when tested | (Successful restores ÷ Total restore tests) × 100 | 99% or higher |
| Security Control Coverage % | How much of your business is protected by security tools | (Protected assets ÷ Total business assets) × 100 | 90% or higher |
| SIEM False Positive Rate | How often are security alerts false alarms | (False alerts ÷ Total alerts) × 100 | Under 10% |
Note: Your cybersecurity plan needs yearly checkups, just like your business needs annual financial reviews to stay healthy. Download this security posture assessment checklist and get started with your annual cybersecurity review.
From Security Zero to Cyber Hero: Your 30-Day Launch Sequence
You now have a clear path forward. Most businesses fail because they never start. Don’t be one of them.
Your cybersecurity plan doesn’t need to be perfect on day one. It needs to exist and improve over time. Start with these basics and build from there.
Your 30-Day Action Plan
Transform your security posture from vulnerable to vigilant with this practical month-long roadmap that delivers absolute protection fast.
As a top-rated cybersecurity consultant, Excellent Webworld has helped hundreds of businesses build practical security plans. We use AI-powered tools and cloud solutions to make cybersecurity simple and affordable.
Download our free cybersecurity template to track your progress. Still need help getting started? We offer a free 30-minute consultation to review your specific risks.

Article By
Mayur Panchal is the CTO of Excellent Webworld. With his skills and expertise, He stays updated with industry trends and utilizes his technical expertise to address problems faced by entrepreneurs and startup owners.